8 Security Aspects
Conditions d’achèvement
Algorithms for Authentication and Key Derivation
Quintessence
of the authentication is the algorithm A3 processed
by the mobile station as well as in the network. In the network a random number
RAND is generated and sent to the MS.
This RAND is constantly changed to protect it against interception and
to enhance the security, because the RAND is only valid for a short
time. The algorithm A3 calculates the 32 bits signature SRES (Signed RESult) from
the secret key Ki and the 128 bits RAND. The calculation of SRES is done independently in AuC and
MS. The SRES calculated in the MS is
sent to the network where it is compared to that SRES calculated in the network. The authentication is successful if
both SRES are identical.
Because SRES could be intercepted on the air interface, the random number RAND is part of the algorithm, so that SRES changes with each new calculation. One can see that keeping Ki secret is the key issue for security. In general, even the user does not explicitly know the Ki.
The
general authentication procedure with A3 is shown in Figure 8-1. The algorithm A3 is operator dependent but has a
general structure:
A3 is a one-way function, i.e. SRES is easy to derive from Ki and RAND, but Ki cannot be derived from SRES and RAND without unaffordable effort even if more than one SRES and RAND pair is known. The length of Ki can be set individually; the 128 bits is only necessary for transfer inside the network. The choice of a shorter Ki weakens the system’s security. If Ki would be transferred the calculation has to be made in the VLR, which therefore would need to have all A3 implementations of all different operators. Also every transfer of Ki brings a risk of interception from attackers. This is why in most networks only the AuC calculates the algorithms and delivers the results to the VLR. To fasten authentication RAND and SRES can be derived in advance in the network. The AuC calculates a set of n (RAND; SRES) pairs for each user and stores it in the HLR.
If needed they are transferred to the VLR. The VLR stores them. For each authentication only one pair is used and thrown away afterwards. The VLR asks the HLR for new pairs if it runs out of pairs. All pairs from the HLR come from the AuC thus Ki never is transferred. The VLR can give unused pairs to the next VLR if the MS changes its location area.
Besides RAND and SRES the AuC also calculates a 64 bits ciphering key Kc with algorithm the A8. The calculations are made in one step together with A3 as both have Ki and RAND as input parameter. Kc is also stored in the HLR.
The key Kc is used for data encryption. The calculation of Kc is also shown in Figure 8-1. It follows the scheme of authentication, but the result is named Kc instead of SRES and is taken for encryption instead of comparison.
A3 and A8 can be derived with one combined algorithm, giving 96 bit that are divided into 32 bit SRES and 64 bit Kc. The combined algorithm usually produces 128 bit from which SRES is the first 32 bit and Kc the last 64 bit.
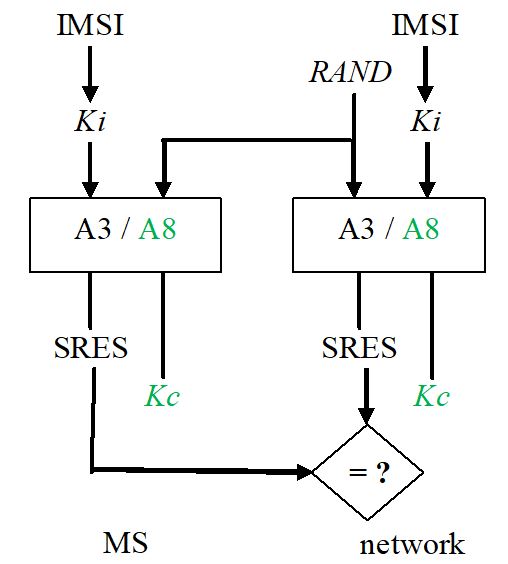
Figure 8-1: Principles of algorithm A3 and A8.
Because SRES could be intercepted on the air interface, the random number RAND is part of the algorithm, so that SRES changes with each new calculation. One can see that keeping Ki secret is the key issue for security. In general, even the user does not explicitly know the Ki.
A3 is a one-way function, i.e. SRES is easy to derive from Ki and RAND, but Ki cannot be derived from SRES and RAND without unaffordable effort even if more than one SRES and RAND pair is known. The length of Ki can be set individually; the 128 bits is only necessary for transfer inside the network. The choice of a shorter Ki weakens the system’s security. If Ki would be transferred the calculation has to be made in the VLR, which therefore would need to have all A3 implementations of all different operators. Also every transfer of Ki brings a risk of interception from attackers. This is why in most networks only the AuC calculates the algorithms and delivers the results to the VLR. To fasten authentication RAND and SRES can be derived in advance in the network. The AuC calculates a set of n (RAND; SRES) pairs for each user and stores it in the HLR.
If needed they are transferred to the VLR. The VLR stores them. For each authentication only one pair is used and thrown away afterwards. The VLR asks the HLR for new pairs if it runs out of pairs. All pairs from the HLR come from the AuC thus Ki never is transferred. The VLR can give unused pairs to the next VLR if the MS changes its location area.
Besides RAND and SRES the AuC also calculates a 64 bits ciphering key Kc with algorithm the A8. The calculations are made in one step together with A3 as both have Ki and RAND as input parameter. Kc is also stored in the HLR.
The key Kc is used for data encryption. The calculation of Kc is also shown in Figure 8-1. It follows the scheme of authentication, but the result is named Kc instead of SRES and is taken for encryption instead of comparison.
A3 and A8 can be derived with one combined algorithm, giving 96 bit that are divided into 32 bit SRES and 64 bit Kc. The combined algorithm usually produces 128 bit from which SRES is the first 32 bit and Kc the last 64 bit.
Figure 8-1: Principles of algorithm A3 and A8.
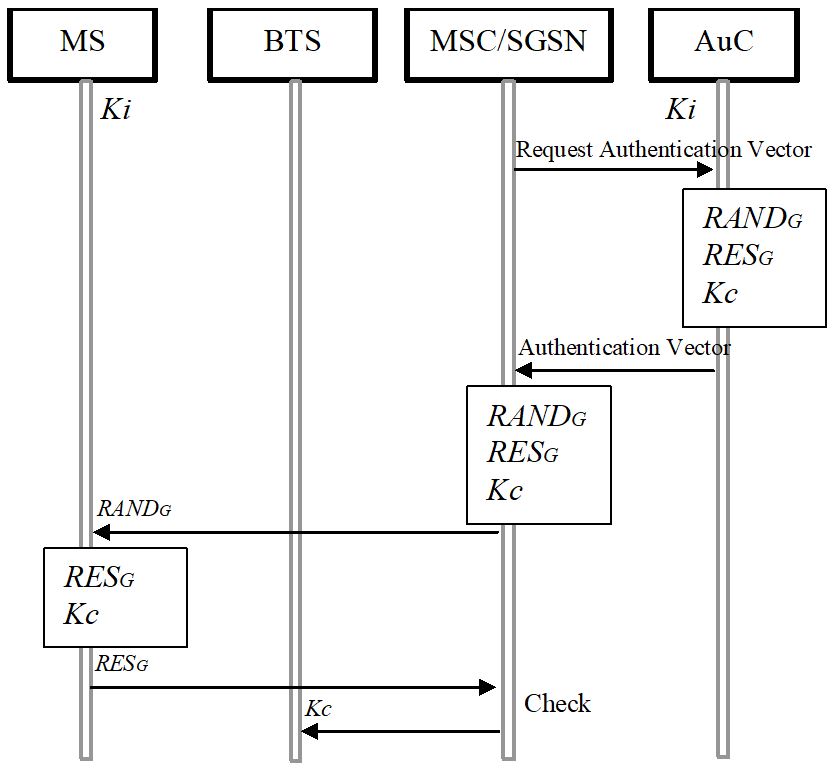
Before a
communication link is established, the user has to be authenticated by the
network. The authentication process uses the identity data described above. These
data are transferred to the MSC to be used for a challenge-response procedure.
The MSC challenges the MS by sending the RAND. The MS calculates the
signed response SRES and sends it back to the MSC. If both RES are
identical, the authentication is completed and ciphering and user data transfer
may begin. This procedure is shown in Figure 8-2.
Figure 8-2: Authentication till start of encryption in GSM.