8 Security Aspects
Completion requirements
8.2 Protection of User Identity and Confidentiality
It
should be ensured that unauthorized reception of signaling over the air
interface does not lead to the knowledge which user occupies which resources in
the network. Calls shall not give information about the user. Also localization
and tracking should be avoided. To achieve this, the IMSI should not be sent in
clear. Most of the time a TMSI (Temporary
Mobile Station Identity) can be used instead. This temporary identity only
is unique when combined with a LAI (Location
Area Identity). This means it only is valid locally and the combination
IMSI-TMSI/LAI is stored in VLR.
A new TMSI is assigned by the VLR after a change of location area (e.g. location update). Therefore, the MS contacts the new VLR with its old LAI and old TMSI. The VLR assigns a new TMSI that is sent encrypted giving additional security (cf. Chapter 7.2).
As long as the mobile station stays in the same location area, only part of the TMSI has to be transmitted (without LAI). This part in comparison to nine octets TMSI only has four octets. This saves resources on the air interface and enables e.g. paging of twice as many stations with one call as when using the complete TMSI.
If part of the VLR data is lost or if data is lost on the air interface, the IMSI has to be transferred in clear, because without identity encryption cannot start. But also it is possible to ask the former VLR about the TMSI, if the LAI is known.
On the transmitter side - after channel coding and interleaving (cf. Chapter 10) - encryption is inserted directly before modulation. Decryption in the receiver starts after demodulation. Therefore, A8 derives from RAND and Ki the cipher key Kc for each connection or transaction (see above).
Kc and the TDMA frame number are input data for the ciphering algorithm A5 for symmetric encryption of the user data (i.e. ciphering and deciphering are done by the same key Kc and algorithm A5) (Figure 8-3). A5 is a stream cipher very efficiently implemented in hardware. There exist different versions, some stronger and some weaker.
Kc is calculated for every authentication and is stored if not used. Signaling and user data are encrypted in the same way, but only on the radio link. For encryption a bit stream is calculated and bit-by-bit binary added to the data stream with both of length 114 bit. Deciphering is done by XOR (eXclusiv OR) of ciphered data stream and key stream.
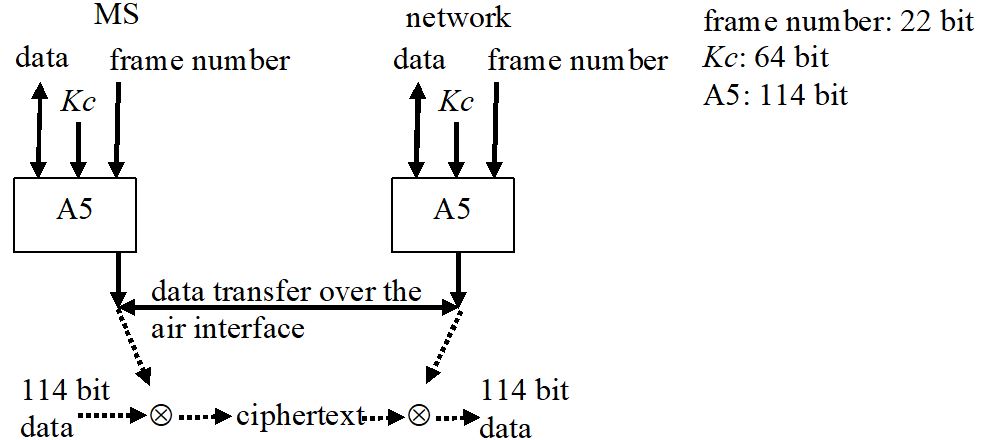
Figure 8-3: Principle of algorithm A5.
The algorithm A5 besides Kc also uses the number of the actual TDMA frame (Time Division Multiple Access) broadcasted by the SCH (Synchronization Channel). That is the way of synchronizing ciphering and deciphering. A repetition of the same frame number during one call is not realistic as one hyper frame takes three and a half hours. The deciphering has to start at an exact point in time. The network controls the beginning directly after authentication as soon as Kc is known. The network asks the MS to start encryption/decryption and itself starts decryption. As soon as the network could decrypt a ciphered message of the MS itself starts the cipher mode.
The algorithm A5 in contrast to A3 and A8 has to be internationally standardized, because otherwise roaming would not be possible (A5 is implemented in the base station). Only the external specifications for A5 are known: 22 bits frame number and 64 bits Kc as input parameters producing two 114 bits output streams. A5 has to be designed in a way that from encrypted data neither Kc nor the original data can be derived without knowledge of A5. Today there are European and Non-European implementations of the algorithms that both have not been published but are publicly known by now. This weakens the security.
A new TMSI is assigned by the VLR after a change of location area (e.g. location update). Therefore, the MS contacts the new VLR with its old LAI and old TMSI. The VLR assigns a new TMSI that is sent encrypted giving additional security (cf. Chapter 7.2).
As long as the mobile station stays in the same location area, only part of the TMSI has to be transmitted (without LAI). This part in comparison to nine octets TMSI only has four octets. This saves resources on the air interface and enables e.g. paging of twice as many stations with one call as when using the complete TMSI.
If part of the VLR data is lost or if data is lost on the air interface, the IMSI has to be transferred in clear, because without identity encryption cannot start. But also it is possible to ask the former VLR about the TMSI, if the LAI is known.
On the transmitter side - after channel coding and interleaving (cf. Chapter 10) - encryption is inserted directly before modulation. Decryption in the receiver starts after demodulation. Therefore, A8 derives from RAND and Ki the cipher key Kc for each connection or transaction (see above).
Kc and the TDMA frame number are input data for the ciphering algorithm A5 for symmetric encryption of the user data (i.e. ciphering and deciphering are done by the same key Kc and algorithm A5) (Figure 8-3). A5 is a stream cipher very efficiently implemented in hardware. There exist different versions, some stronger and some weaker.
Kc is calculated for every authentication and is stored if not used. Signaling and user data are encrypted in the same way, but only on the radio link. For encryption a bit stream is calculated and bit-by-bit binary added to the data stream with both of length 114 bit. Deciphering is done by XOR (eXclusiv OR) of ciphered data stream and key stream.
Figure 8-3: Principle of algorithm A5.
The algorithm A5 besides Kc also uses the number of the actual TDMA frame (Time Division Multiple Access) broadcasted by the SCH (Synchronization Channel). That is the way of synchronizing ciphering and deciphering. A repetition of the same frame number during one call is not realistic as one hyper frame takes three and a half hours. The deciphering has to start at an exact point in time. The network controls the beginning directly after authentication as soon as Kc is known. The network asks the MS to start encryption/decryption and itself starts decryption. As soon as the network could decrypt a ciphered message of the MS itself starts the cipher mode.
The algorithm A5 in contrast to A3 and A8 has to be internationally standardized, because otherwise roaming would not be possible (A5 is implemented in the base station). Only the external specifications for A5 are known: 22 bits frame number and 64 bits Kc as input parameters producing two 114 bits output streams. A5 has to be designed in a way that from encrypted data neither Kc nor the original data can be derived without knowledge of A5. Today there are European and Non-European implementations of the algorithms that both have not been published but are publicly known by now. This weakens the security.